Cloud Computing Security And Its Challenges
Through the Internet, cloud solutions offer on-demand IT resources. They go by the names cloud computing and cloud services occasionally. It gives the users access to everything from apps to data centres. Both businesses and end users can benefit from cloud-based solutions. Pay-as-you-go cloud service providers guarantee that businesses only ever pay for the resources they really utilize. Cloud solutions provide fast, on-demand access to pools of shared IT resources, which helps businesses save costs, enhance productivity, and rebalance capital and operational spending. They also provide data confidentiality as part of your cybersecurity threat prevention.
Cloud Computing has become popular among individuals who require larger storage space and also for businesses that are seeking an efficient off-site backup solution. The data which is stored on physical servers, are maintained by a reliable cloud service provider. This helps eliminate the requirement for organizations to self-manage the physical resources themselves.
Cloud computing is very beneficial for both the individual and the businesses. Some of its benefits are that it is cost-effective, increases speed and agility, unlimited scalability, enhances strategic value, agility elasticity, and many more. In this blog post, we will cover cloud computing security challenges.
Major Security Challenges In Cloud Computing
Cloud services providers become much more reliant on the cloud infrastructure to run their business applications, security threats have the potential to impact the cloud computing software.
When cloud computing evolves or updates, security threats also keep changing, as do your IT resources need to. Cloud service providers always try to constantly update the threat landscape but the security threat evolves and new threats emerge daily. Some of the major security challenges are mentioned below.
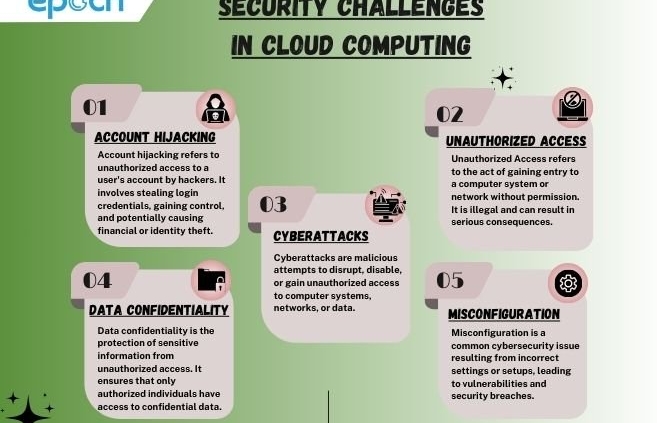
ACCOUNT HIJACKING IN CLOUD COMPUTING
Several years back there was an era where the employees had to be physically present in the office for their respective work. But nowadays because of the cloud applications like Google Workspace users can log on to their workplace applications anywhere, anytime, and from any device. Undoubtedly this flexibility provides a major benefit for workplace productivity but yes this also comes with a high risk of cloud account hijacking.
Hijacking of an account of the user is one of the major cloud computing issues for companies across sectors. Using cloud-based services or applications will definitely increase the risk of account hijacking. So mainly users must be careful about protecting their passwords and confidential information to always stay secure in the cloud.
UNAUTHORIZED ACCESS
Unauthorized access to the data is one of the most common cloud security issues generally faced by businesses. Cloud computing provides an easy way for businesses to store data, which can sometimes also lead to cyber threats of unauthorized access to the data. Unauthorized access to the user’s data can lead to the theft of data and malware attacks. Improper configuration of data security can enable some attackers to have unauthorized access to the company’s private data.
As data is a very important component for every individual or company it is very important that only authorized users can access it. Implementing data security is a way or procedure by which businesses safeguard their data from unauthorized access.
CYBERATTACKS
Protecting data from cyberattacks is a major concern for every company. The problem of cyberattacks is a real worry for both individuals and businesses who are using the services of cloud computing. Attackers always use weak points in cloud infrastructure or applications. This usually leads to the misuse of user’s data. By simply understanding the risk and properly implementing security measures, businesses can safeguard their data.
DATA CONFIDENTIALITY
Cloud Computing provides a feature of data storage. So that businesses or individual can access their data from anywhere at any time. Data privacy or configuration in basic words means to keep the data private and it should not be accessed by any other unauthorized user. We know data is a very important component for both individuals and businesses. So keeping that private automatically becomes a major concern in cloud computing. Always use security best practices to ensure data confidentiality.
<p><p><p><p><p><p>Organizations do not have control over who can access their data so they always ensure that only authorized users get access to it. Data breaches usually happen when somehow hackers are able to access private data. In the upcoming year data privacy issues will be even more because the use of cloud computing will increase.
MISCONFIGURATION
This is one of the major security threats or challenges that are faced in cloud computing. Misconfiguration generally leads to glitches or errors that could appear while using cloud computing. Users must ensure that their data is protected and the applications are configured correctly so that there will be fewer chances of their data getting misconfigured. The Correct usage of the applications and software users can safeguard against the threat of misconfiguration
<p><strong>In Conclusion, Cloud computing provides various features and advantages to individuals and businesses but at the same time, it also has to deal with many security threats. When cloud computing evolves or updates, security threats also keep changing. Cloud-based infrastructure faces many security challenges as data privacy or confidentiality, cyberattacks, and misconfiguration. As well as account hijacking, internal and external threats, unauthorized access, lack of visibility, and many more. Users can safeguard their data from these threats by protecting their passwords and confidential information to always stay secure in the cloud.