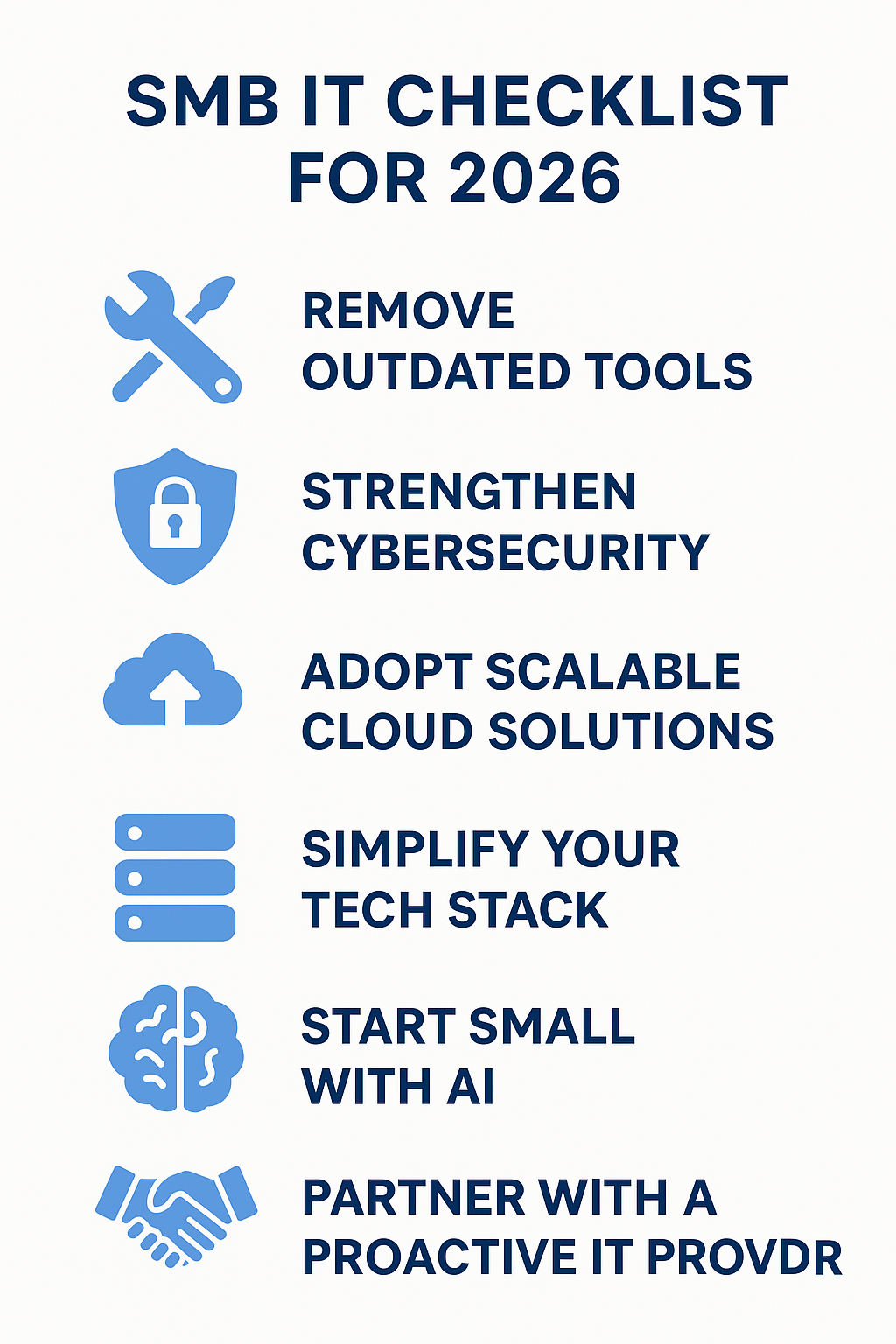
IT infrastructure services are essential to any organization and encompass hardware, software, networking, and data storage. They ensure a secure, efficient, and reliable IT environment, improving operations, collaboration, and data management while reducing downtime. Key components such as servers and networking tools handle data storage, processing, and security, thereby optimizing system performance. Through services such as network management, server administration, and disaster recovery, businesses build a resilient IT ecosystem and deliver the best IT support in Allentown, PA. These solutions, including cloud computing and data protection, support seamless, scalable IT operations that adapt to changing business needs.
Understanding IT Infrastructure Services and Their Importance
IT infrastructure services are crucial for organizations aiming to optimize their technological operations. These services include hardware, software, networking systems, and data storage solutions necessary to maintain a company’s IT environment. By utilizing these services, businesses can streamline internal processes, promote efficient team collaboration, enhance data handling, and scale to meet future demands. Furthermore, investing in robust IT infrastructure services can lead to significant long-term savings by reducing downtime, boosting productivity, and mitigating the risks associated with outdated or inefficient technology.
Key Components and Functions of IT Infrastructure Services
The effectiveness of IT infrastructure services depends on a range of critical components working together seamlessly. These include servers, storage systems, networking devices, and software applications, all of which provide essential functions such as data processing, communication, and storage. Other vital functions encompass data backup, network security, system monitoring, and resource management. By understanding the interrelationship between these components, IT professionals can design, implement, and manage a comprehensive IT infrastructure that supports optimal performance, security, and efficiency. When properly managed, these services ensure a stable, responsive, and secure IT environment.
Network Management for Optimized IT Infrastructure
Network management is a vital aspect of IT infrastructure, ensuring smooth and uninterrupted connectivity across all systems. It involves monitoring and optimizing network resources to address challenges such as bandwidth limitations, network congestion, and security risks. Implementing advanced network management tools, such as performance monitoring software and configuration management systems, can help detect and resolve issues quickly, ensuring consistent and reliable network performance. By enhancing network reliability, scalability, and security, businesses can support a seamless, high-performing IT ecosystem that aligns with their operational goals.
Effective Server Administration
Efficient server administration is fundamental to maintaining a secure, high-performance IT infrastructure. It requires a proactive approach to software updates, server monitoring, and security implementation. Regular software updates and prompt application of security patches are crucial for preventing vulnerabilities. Server administration also involves resource optimization and ensuring that the server environment can handle peak workloads without performance degradation. Additionally, implementing backup systems and disaster recovery plans ensures that businesses can maintain continuity in the event of unforeseen disruptions. Through meticulous server management, organizations can safeguard the integrity and efficiency of their IT infrastructure.
Strengthening Data Security Measures
Data security is a cornerstone of IT infrastructure, ensuring the confidentiality, integrity, and availability of sensitive information. Key measures to safeguard data include:
- Access Control: Use role-based access and multi-factor authentication to restrict unauthorized access.
- Encryption: Employ encryption for both data at rest and data in transit to protect against unauthorized access.
- Regular Audits: Perform continuous audits to track data access and modifications, promptly identifying potential security threats.
- Employee Training: Provide ongoing training on data security practices to minimize human error and security breaches.
By integrating these security practices, businesses can protect their data, enhance trust with stakeholders, and ensure compliance with regulatory standards.
Disaster Recovery Solutions for Business Continuity
A comprehensive disaster recovery plan is essential for maintaining business continuity in the event of a disruption. This plan should include strategies for data backup, replication, and restoration to protect critical business data from system failures, cyber threats, or natural disasters. Key elements of a disaster recovery plan include identifying essential processes, prioritizing recovery efforts, and establishing effective communication channels. Additionally, regular testing of the recovery plan ensures its efficacy and allows organizations to adapt to evolving threats. Cloud-based solutions offer scalable and cost-effective off-site data recovery options, helping organizations quickly restore operations in the face of unexpected challenges. By investing in disaster recovery, businesses can safeguard their digital assets, minimize downtime, and enhance operational resilience.
Contact Us
At Epoch IT, we’re here to support your business with expert IT solutions. Whether you need immediate assistance, have questions about our services, or want to explore training opportunities, reaching out is easy.
📞 Phone: (610) 841-4932
🏢 Office Locations: 4295 Tilghman St Ste 201, Allentown, PA 18104
🕒 Office Hours:
- Monday – Friday: 8 AM – 5 PM
🌐 Online Contact Form: Prefer to write? Please fill out our contact form, and a member of our team will get back to you shortly.
Related Topics: